Achieving ISO 27001 certification: Tips and guidance

In an era where data breaches and cybersecurity risks are omnipresent, businesses need more than just a robust IT infrastructure to protect their sensitive information.
ISO 27001, one of the most recognized information security standards globally, provides a systematic approach to managing and safeguarding data assets.
This comprehensive guide will take you through the intricacies of ISO 27001 certification, equipping you with the advice and guidance necessary for your organization to achieve this prestigious recognition.
Understanding ISO 27001
What is ISO 27001?
ISO 27001 is an international standard for Information Security Management Systems (ISMS).
It is published by the International Organisation for Standardisation (ISO) and the International Electrotechnical Commission. ISO 27001 consists of 114 controls that are divided into 14 categories.
Implementing the full list of ISO 27001's controls is not mandatory since they are simply a representation of possibilities that an organization may consider. ISO 27001 offers a systematic approach to managing sensitive information, ensuring its confidentiality, integrity, and availability.
An ISO 27001-certified ISMS can provide significant competitive advantages, such as increased customer trust, a competitive edge in the market, and reduced security risks.
Who needs ISO 27001 certification?
ISO 27001 certification is relevant to a wide range of organizations. Whether you're a small business handling sensitive customer data, a multinational corporation with global operations, or a government agency, ISO 27001 can be tailored to fit your specific requirements. As the standard is versatile and scalable, it's a viable choice for any entity that values the security of its information.
ISO 27001 certification cost
The cost of obtaining ISO 27001 certification can vary significantly based on several factors. One of the most significant considerations is the size and complexity of your organization.
Larger companies with extensive operations and information systems may face higher costs due to the sheer scale of implementation. Moreover, the industry in which your organization operates plays a role, with highly regulated sectors often incurring greater expenses to meet compliance requirements.
The cost breakdown typically includes expenses related to hiring consultants or experts for guidance, internal resource allocation, and the implementation of security measures. This may involve investing in new technologies, strengthening existing systems, and providing employee training.
Additionally, there are expenses associated with the actual certification process, such as assessment and audit fees. It's essential for organizations to carefully evaluate these factors and budget accordingly to make the ISO 27001 certification journey as cost-effective as possible.
Benefits of ISO 27001 certification

ISO 27001 certification offers a plethora of advantages for organizations of all sizes and sectors. By implementing this standard, you demonstrate your commitment to data security and the highest industry standards.
- Enhanced information security: ISO 27001 helps you establish a robust information security management system, reducing the risk of data breaches and cyberattacks.
- Legal and regulatory compliance: It assists in ensuring compliance with data protection laws and regulations such as those exerted by European Union’s General Data Privacy Regulation (GDPR) and the United States’ Health Insurance Portability and Accountability Act (HIPAA), avoiding legal issues and associated penalties.
- Risk management: ISO 27001 provides a systematic approach to identifying, assessing, and mitigating security risks.
- Improved customer trust: Certification demonstrates your commitment to safeguarding customer data, enhancing their trust in your organization.
- Competitive advantage: It sets you apart from competitors who lack ISO 27001 certification, potentially attracting more customers.
- Reduced security incidents: A well-implemented ISMS can lead to a decrease in security incidents and their associated costs.
- Cost savings: Efficient risk management can result in savings, such as reduced insurance premiums and data breach-related expenses.
- Business continuity: ISO 27001 helps create effective business continuity plans, ensuring operations continue even during security incidents.
- Increased organizational efficiency: It encourages the optimization of processes and resource allocation.
- Employee awareness: ISO 27001 promotes a security-conscious culture, making employees more vigilant about data security.
- International recognition: ISO 27001 is globally recognized, facilitating international business relations.
- Stakeholder confidence: It instills confidence in shareholders, partners, and investors regarding your security measures.
- Better vendor relationships: Certified organizations are often preferred by vendors and partners concerned about data security.
- Continuous improvement: ISO 27001 encourages a cycle of improvement through regular audits and reviews.
- Demonstrated commitment: Certification reflects your dedication to information security, making it easier to attract and retain talent.
- Protection of intellectual property: Safeguarding sensitive data, including intellectual property, is a crucial aspect of ISO 27001.
- Cyber insurance eligibility: Certification can improve eligibility for cyber insurance, reducing financial risk.
- Adherence to best practices: ISO 27001 aligns your security practices with industry best standards.
- Security in outsourcing: It helps manage risks when outsourcing processes or data handling to third parties.
- Proactive approach: ISO 27001 promotes a proactive, rather than reactive, stance towards security
Remember, the specific benefits may vary depending on your organization's size, industry, and how effectively you implement ISO 27001.
ISO 27001 certification process: How to get ISO 27001 certification
The ISO 27001 certification process is a structured approach that aims to help organizations establish a robust ISMS. It includes a series of steps and assessments designed to ensure that an organization's data and information assets are adequately protected.
Achieving ISO 27001 certification involves several key steps:
1. Gap analysis
This critical starting point requires a meticulous examination of your organization's existing information security practices.
The gap analysis phase involves evaluating the effectiveness of your current security measures and identifying areas that do not meet ISO 27001 standards.
This process often includes a comprehensive review of security policies, procedures, risk management practices, and control mechanisms. The insights gained from this analysis serve as a roadmap for refining your information security framework.
2. ISMS establishment
Building your Information Security Management System (ISMS) is the cornerstone of ISO 27001 certification. This involves creating a structured system that aligns with ISO 27001 standards.
The ISMS encompasses a range of components, such as security policies, risk assessment methodologies, defined procedures for incident management, and an array of security controls tailored to your organization's specific needs.
The development of a robust ISMS requires a methodical approach and the integration of security practices into your organizational culture.
3. Risk assessment
A thorough risk assessment is a pivotal aspect of ISO 27001 certification. This phase involves identifying, analyzing, and evaluating potential threats and vulnerabilities to your organization's data assets.
This comprehensive risk assessment provides a nuanced understanding of the security landscape, enabling your organization to develop proactive security measures and incident response strategies. It serves as a basis for determining the security controls necessary to mitigate risks effectively.
4. Documentation
Documentation is a cornerstone of ISO 27001 certification, ensuring transparency and compliance. It involves the creation of extensive records detailing your ISMS components, risk assessment results, policies, procedures, and controls.
Central to this documentation is the Statement of Applicability (SoA), a comprehensive report that specifies which ISO 27001 controls are applicable to your organization's specific context.
Effective documentation is vital for demonstrating adherence to ISO 27001 standards during the certification audit.
5. Training and awareness
Building a culture of security awareness within your organization is paramount. This step involves developing training programs and initiatives that ensure all employees are well-versed in information security practices.
Employee awareness extends beyond understanding security policies; it emphasizes individual responsibility in safeguarding data and reporting security incidents promptly. By fostering a security-conscious workforce, you enhance the overall effectiveness of your ISMS.
Ensure that all employees are adequately trained and aware of their roles in maintaining information security.
6. Internal audit
Regular internal audits are a crucial self-assessment mechanism. These audits are conducted to gauge how well your ISMS aligns with ISO 27001 standards.
Internal audits offer insights into your system's performance, highlighting areas of compliance and potential non-conformities. They provide opportunities to identify and address weaknesses, ultimately enhancing the effectiveness of your information security measures.
Components of Internal Audits
During internal audits, the following components should be included:
- Compliance Verification: Internal audits should ensure that your ISMS aligns with the ISO 27001 standards. This includes verifying that your security policies, procedures, and controls comply with the defined requirements.
- Risk Assessment Validation: Auditors should assess whether your risk assessment methodologies are comprehensive and that potential threats and vulnerabilities have been adequately considered.
- Control Effectiveness: Evaluate the effectiveness of the security controls in place. This includes reviewing access controls, encryption mechanisms, intrusion detection systems, and other protective measures to ensure they perform as intended.
- Documentation Review: The internal audit should encompass a review of the extensive documentation associated with your ISMS. This includes the Statement of Applicability (SoA) and other records outlining your policies, procedures, and controls.
Types of internal audits
Internal audits come in various types, each serving a specific purpose. The key types of internal audits include:
- Compliance Audits: These audits primarily focus on ensuring that your ISMS is in compliance with ISO 27001 standards. Auditors assess whether the ISMS components adhere to the defined requirements.
- Risk-Based Audits: These audits are centered on assessing the effectiveness of your risk assessment and management processes. They help in identifying and mitigating potential risks and vulnerabilities.
- Control Audits: Control audits are designed to evaluate the functionality and efficacy of your security controls. They assess whether the implemented controls adequately safeguard data assets and mitigate risks.
- Documentation Audits: These audits focus on the completeness and accuracy of documentation related to your ISMS. Auditors ensure that records are well-maintained and provide comprehensive insights into your information security practices.
- Operational Audits: These audits dive into the day-to-day operational aspects of your ISMS. They assess how well your security policies and procedures are implemented in real-world scenarios.
- Policy Audits: Policy audits specifically review your security policies to ensure they are well-defined, up-to-date, and aligned with ISO 27001 requirements.
By incorporating these elements and types of internal audits, your organization can maintain a rigorous evaluation process, ensuring the continual effectiveness of your ISMS and a smoother path to ISO 27001 certification.
7. Corrective actions
The final phase revolves around addressing any non-conformities and deficiencies uncovered during the internal audit. Corrective actions are pivotal in rectifying deviations from ISO 27001 standards.
This phase ensures that your ISMS aligns with certification requirements and remains effective over time. It's an ongoing process of improvement and refinement that continues well beyond achieving ISO 27001 certification.
8. Certification audit
Engage an accredited certification body to conduct a certification audit to determine your organization's compliance with ISO 27001 standards.
An accredited certification body refers to an independent organization that holds accreditation for conducting certification audits in accordance with ISO 27001 standards.
These organizations are authorized and recognized for their competence and impartiality in assessing an organization's compliance with ISO 27001. Engaging an accredited certification body ensures that the audit process is reliable and credible.
There are several accredited certification bodies around the world that can conduct ISO 27001 certification audits. Some examples include:
- Bureau Veritas
- DNV GL
- TÃœV SÃœD
- BSI Group
- SGS
- Intertek
- DEKRA
- LRQA (Lloyd's Register Quality Assurance)
- NSF International
- Aprio
Please note that the availability of these bodies may vary by location, so it's important to check for certification bodies accredited in your specific region. Accreditation is typically granted by relevant national accreditation bodies.
9. Certification
Upon successful completion of the audit, your organization will be awarded ISO 27001 certification.
Common challenges during ISO 27001 certification

While the ISO 27001 certification process is highly beneficial, it can be challenging. Common challenges include:
1. Balancing security requirements with operational needs
Achieving ISO 27001 certification often involves striking a balance between stringent security measures and the operational needs of your organization. This challenge requires a thoughtful approach to ensure that security doesn't hinder day-to-day operations.
2. Engaging and educating employees on information security
Employees play a pivotal role in information security, but ensuring their active engagement and understanding can be challenging. Education and awareness programs are essential to help employees recognize their role in maintaining a secure environment.
3. Meeting documentation and procedural requirements
ISO 27001 places considerable emphasis on documentation and documented procedures. This can be challenging, as it requires comprehensive documentation of policies, procedures, risk assessments, and more. Maintaining this documentation accurately and keeping it up to date is an ongoing challenge.
4. Ensuring that the ISMS remains effective over time.
Implementing an ISMS is not a one-time task. Ensuring that your ISMS remains effective over time requires continuous monitoring, regular audits, and updates to keep it aligned with evolving security risks and changing business needs.
5. Resource allocation
Allocating resources to information security efforts, especially in smaller organizations, can be challenging. It's important to allocate both human and financial resources effectively to achieve certification without straining your organization.
6. Integration with existing systems
Organizations with established processes and systems might face challenges when integrating ISO 27001 requirements seamlessly. The certification process involves aligning existing practices with the ISO standard, which can be a complex task.
7. Scope definition
Determining the scope of your ISMS is a critical yet challenging step. Defining the boundaries of the ISMS and understanding what is included and excluded can sometimes be tricky.
8. Complexity of risk assessment
Conducting a thorough risk assessment can be complex, as it requires identifying vulnerabilities, assessing potential threats, and calculating risks. The challenge lies in creating a comprehensive risk management strategy.
9. Change management
Implementing changes in policies, procedures, and practices to meet ISO 27001 requirements can meet resistance from employees and may disrupt established workflows. Effective change management is key to addressing this challenge.
10. Resistance to cultural change
Shifting the organizational culture to prioritize information security can face resistance from employees accustomed to a different mindset. Encouraging a security-conscious culture is an ongoing challenge.
Overcoming these challenges requires a strategic and committed approach, emphasizing the value of ISO 27001 certification and ensuring that it aligns with your organization's specific needs and objectives.
Tips to obtain an ISO 27001 certification
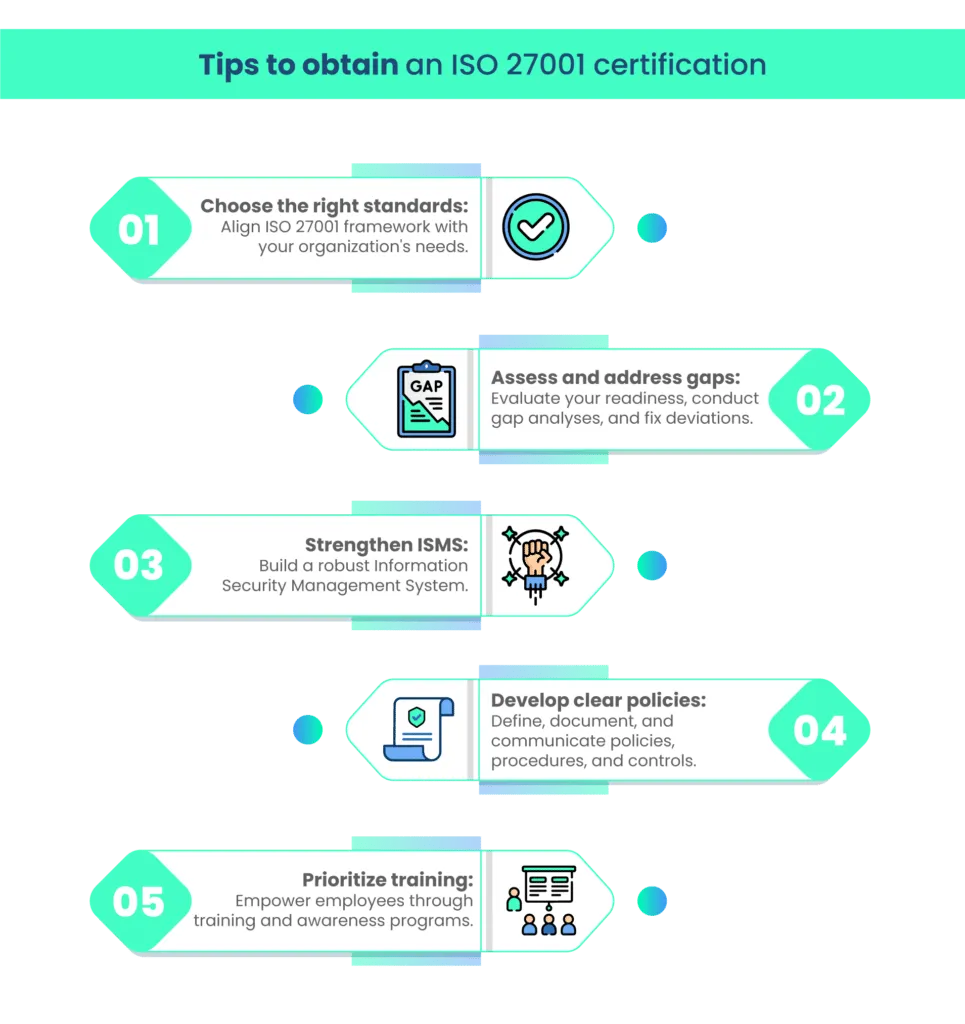
Maintaining ISO 27001 certification
ISO 27001 certification is not a one-time achievement but an ongoing commitment. Develop a plan for maintaining certification by continuously improving your ISMS, addressing non-conformities, and staying vigilant against emerging threats.
Wrapping up
Embarking on the ISO 27001 certification journey is a significant step towards fortifying your organization's information security. While it may seem like a daunting path, remember that with the right guidance, such as the tips and guidance shared in this blog, the process becomes more manageable.
Achieving ISO 27001 certification not only ensures that you meet internationally recognized standards but also demonstrates your unwavering commitment to safeguarding sensitive data and bolstering your cybersecurity posture.
So, take these tips to heart, prepare your team, and chart your course towards certification with confidence.
Frequently Asked Questions (FAQs)
1. What is ISO 27001 certification, and why is it important for organizations? ISO 27001 certification is an internationally recognized standard for information security management systems. It's crucial for organizations because it helps protect sensitive data, enhance cybersecurity, and build trust with clients and partners.
2. What are the common challenges during ISO 27001 certification? Common challenges during ISO 27001 certification include balancing security requirements with operational needs, engaging and educating employees on information security, meeting documentation and procedural requirements, and ensuring the ISMS remains effective over time.
3. How can organizations choose the right ISO 27001 framework and standards? To choose the right ISO 27001 framework and standards, organizations should consider alignment with their business goals and operational requirements. They can select a framework that best fits their industry and compliance needs.
4. What is the role of the ISMS in ISO 27001 certification? The ISMS is a cornerstone of ISO 27001 certification. It includes security policies, procedures, and controls tailored to an organization's specific needs, ensuring comprehensive data protection.
5. What are the key benefits of achieving ISO 27001 certification for organizations? The key benefits of achieving ISO 27001 certification include improved data security, reduced risk of data breaches, enhanced business reputation, better compliance with data protection regulations, and increased competitiveness in the market. This certification not only safeguards organizations but also reassures clients and partners of their commitment to information security.


















